Role of Business Analyst in Application and Data Security
Published by Pavel Nakonechnyy on (updated: ) in Business Analysis.Per BABOK Guide 3rd edition, security is one of the categories of Non-Functional Requirements that, per definition, “augment the functional requirements of a solution, identify constraints on those requirements, or describe quality attributes a solution must exhibit when based on those requirements.” As such, security requirements describe “aspects of a solution that protect solution content or solution components from accidental or malicious access, use, modification, destruction, or disclosure”.
The analyst’s job is to highlight the problems that can arise from ignoring security so that stakeholders recognise them and can make informed decisions. And if a security specialist has given an expert opinion, there is no need to take it as the truth in the last instance. After all, no one knows the system requirements as well as you do, and without a discussion with you and the development team, their advice, even if good in itself, may be useless.
Another source of security requirements may lie in the Legal and Compliance departments. Organizations must adhere to specific regulations that dictate security measures. For instance, laws such as the Health Insurance Portability and Accountability Act (HIPAA) and the Payment Card Industry Data Security Standard (PCI-DSS) impose strict guidelines on how sensitive information should be handled and protected. External security requirements often necessitate implementing robust security controls, including firewalls, intrusion detection systems, and encryption protocols. Though, it usually is not a direct responsibility of the Business Analyst to know industry regulations and standards, being aware of the key concepts and most important pieces of law will benefit your work.
So, as a Business Analyst, you should learn the following things:
- What aspects do you have to cover by Security Requirements;
- Where to look for external Security Requirements;
- What are the usual conflicts of security requirements with other non-functional requirements.
After understanding the specific aspects of security requirements, external sources of information, and the usual conflicts that arise with other non-functional requirements, you will be equipped with the knowledge necessary to navigate the intricacies of security in business analysis effectively. This understanding will lead to robust, secure applications that meet functional and non-functional expectations. We will go through these topics one by one now.
Key Security Requirements for Applications
The Application Security Requirements are going to be specific to your project, but there are standard recommendations on what to consider and decide if applicable or not. From this list, choose applicable ones and be in a position to defend your choices to include or exclude certain aspects.
- Access Control. Access control mechanisms ensure that only authorized users can access specific resources within an application. It includes implementing role-based access controls (RBAC) and ensuring that permissions are granted based on the principle of least privilege. If access control measures are not present, it could lead to unauthorized access and potential data breaches.
- Information Classification. Information classification involves categorizing data based on its sensitivity and the impact of unauthorized disclosure. It helps organizations apply appropriate security controls based on the classification level. If an organization does not classify its information, it may struggle to implement adequate protections for sensitive data.
- Segregation of Duty and Access. Segregation of duties ensures that no single individual controls all aspects of a critical process. It reduces the risk of fraud and error. Lack of Segregation of duties could lead to conflicts of interest and increased risk of malicious activities.
- Resilience Against Malicious Attacks. Applications must be designed to withstand and repel malicious attacks, such as Distributed Denial of Service (DDoS) attacks. It includes implementing security measures like firewalls, intrusion detection systems, and regular security testing. If resilience measures are lacking, applications may be vulnerable to downtime and data loss.
- Legal, Regulatory, and Contractual Requirements. Organizations must comply with applicable laws, regulations, and contractual obligations for data protection and cybersecurity. It includes understanding requirements such as GDPR, HIPAA, or PCI DSS (more on them below). Failure to comply can result in legal penalties and damage to reputation.
- Privacy. Privacy requirements focus on protecting personal data and ensuring that it is collected, processed, and stored in compliance with privacy laws. Without privacy measures, organizations risk violating user trust and legal obligations.
- Data Protection. Data protection involves implementing measures to safeguard data from unauthorized access, loss, or corruption. It includes encryption, access controls, and regular backups. Without proper data protection, sensitive information is exposed to threats.
- Protection of Data Processed, Stored, or Transmitted. This requirement emphasizes the importance of data security at all stages—when it is being processed, stored, or transmitted. It includes using encryption and secure protocols. Otherwise, data may be vulnerable during transmission or storage.
- Input Validation. Input validation ensures that data entered into an application is checked for correctness and security before processing. It helps prevent attacks, such as SQL injection and cross-site scripting (XSS). Without Input Validation, applications may be susceptible to various injection attacks.
- Output Validation. Output validation involves checking data before it is sent to users or external systems to prevent data leakage and ensure it is safe for display. If output validation is overlooked, sensitive information can be inadvertently exposed.
- Restrictions on ‘Open Text’ Fields. Open text fields allow users to input unrestricted data, which can lead to security vulnerabilities. Organizations should implement restrictions and validation in these fields to mitigate risks. If not controlled, these fields create a risk of injection attacks.
- Logging and Monitoring. Logging and monitoring are essential for detecting and responding to security incidents. Organizations should maintain logs of user activities and system events to identify suspicious behaviour. Without proper logging, it becomes challenging to investigate incidents and understand security breaches.
- Non-Repudiation. Non-repudiation ensures that all actions taken within an application can be verified and attributed to specific users. It is crucial for accountability and legal compliance. If non-repudiation measures are absent, it may be impossible to prove who performed particular actions.
- Authorisation Processes and Levels. Establishing strong authorization processes and levels ensures users have appropriate access based on their roles. It helps prevent unauthorized access to sensitive information. If these processes are not defined, it can lead to security gaps.
- Physical Transfers of Media and Documents. Organizations must have procedures for securely transferring physical media and documents containing sensitive information. It includes encryption and secure transport methods. If not addressed, sensitive data can be exposed during physical transfers.
- Data Retention Periods. Data retention policies dictate how long data should be stored and when it should be securely disposed of. It is important for compliance with Legal and Regulatory requirements. If retention periods are not set, organizations may retain data longer than necessary, increasing risk.
- Insurance. Cybersecurity insurance can help mitigate financial losses caused by data breaches and cyber incidents. Organizations should assess their risk exposure and consider obtaining insurance coverage. If insurance is not in place, organizations may face significant financial repercussions in the event of a breach.
- Contractual Requirements. Organizations must adhere to contractual obligations related to data security and privacy. It includes ensuring that third-party vendors comply with the same security standards. Failure to meet contractual requirements can lead to legal disputes and financial losses.
- End of Contract / Relationship. When a contract or relationship ends, organizations must have procedures for securely handling data, including deletion or return of sensitive information. Otherwise, sensitive data may remain exposed after the relationship has ended.
All these security requirements play a vital role in establishing a robust security posture. Organizations should carefully evaluate which requirements apply to their specific context and justify any exclusions. By doing so, they can ensure that their applications and sensitive data are adequately protected against potential threats.
Sources of External Security Requirements
In addition to Security Requirements arising from your organisation’s considerations, some requirements are imposed by Laws, Regulators, or Certification requirements. Let’s review some examples.
Laws Imposing Security Requirements
EU:
- General Data Protection Regulation (GDPR). The GDPR is a comprehensive data protection law in the European Union that imposes obligations regarding data security and privacy. It mandates organizations to implement appropriate technical and organizational measures to ensure data security and protect personal data from breaches.
- ePrivacy Directive. The ePrivacy Directive (2002/58/EC) focuses on privacy and electronic communications. It sets out specific requirements for the security of personal data in electronic communications, including obligations for service providers to ensure the confidentiality of communications and to implement appropriate security measures to protect user data.
- Network and Information Systems Directive (NIS Directive). The NIS Directive (2016/1148) aims to enhance cybersecurity across the EU. It requires member states to adopt national cybersecurity strategies and mandates essential service operators and digital service providers to implement security measures and report incidents to national authorities.
- Digital Operational Resilience Act (DORA). DORA aims to strengthen the IT security of financial entities in the EU. It requires financial institutions to ensure their information and communication technology (ICT) systems are resilient against cyber threats and to conduct regular testing of their ICT systems.
- Regulation on the European Union Agency for Cybersecurity (ENISA). It mandates ENISA to support member states in implementing cybersecurity measures and to provide guidance on best practices for securing networks and information systems.
- Digital Markets Act (DMA). While the DMA does not explicitly outline security requirements, it imposes obligations that indirectly relate to security. For instance, the DMA requires gatekeepers to ensure transparency in their operations, which includes providing information about how they handle user data and advertising practices. This transparency holds companies accountable for their data management and protection strategies.
- Digital Services Act (DSA). The Digital Services Act establishes a framework for online platforms to manage content and protect users with measures such as risk assessments to identify and mitigate risks related to the dissemination of illegal content and other harmful activities, secure handling of user data and mechanisms of reporting illegal content, measures that safeguard personal information against unauthorized access and breaches, and transparency in algorithms.
US:
- Health Insurance Portability and Accountability Act (HIPAA). HIPAA is a U.S. law that sets national standards for health information protection. It requires healthcare providers and related entities to implement security measures to protect electronic health information from unauthorized access, alteration, and destruction.
- California Consumer Privacy Act (CCPA). The CCPA is a state law in California that grants consumers rights over their data and imposes obligations on businesses to ensure data security. It requires organizations to implement reasonable security procedures to protect consumer data from breaches.
- Federal Information Security Management Act (FISMA). FISMA is a U.S. federal law that requires federal agencies to develop, document, and implement an information security program to protect their information systems and data.
- Payment Card Industry Data Security Standard (PCI DSS). PCI DSS is a set of security standards ensuring that all companies that accept, process, store, or transmit credit card information maintain a secure environment. It mandates specific security measures to protect cardholder data.
Regulators Imposing Security Requirements
EU:
- European Data Protection Board (EDPB). The EDPB is an independent European body that ensures consistent application of data protection rules across the EU. It provides guidelines and recommendations on data protection and security measures that organizations must implement to comply with GDPR.
- European Banking Authority (EBA). The EBA develops regulatory and supervisory standards for the banking sector in the EU. It issues guidelines on the security of payment services and the management of operational risks, including cybersecurity risks.
- European Securities and Markets Authority (ESMA). ESMA is responsible for enhancing investor protection and promoting stable and orderly financial markets. It issues guidelines that include requirements for the security of trading platforms and investor data protection.
- European Central Bank (ECB). The ECB oversees the stability of the eurozone’s financial system. It has established security requirements for payment systems and financial institutions to ensure the integrity and security of financial transactions.
- European Medicines Agency (EMA). The EMA regulates the pharmaceutical sector in the EU and imposes security requirements on organizations involved in the development and distribution of medicinal products. It includes ensuring the security of clinical trials and patient information data.
- European Union Agency for Cybersecurity (ENISA). ENISA publishes guidelines and threat landscapes, such as the ENISA Threat Landscape for Supply Chain Attacks, to help organizations understand and mitigate cybersecurity risks in the supply chain.
US:
- National Institute of Standards and Technology (NIST). NIST provides guidelines and standards for information security, including the Secure Software Development Framework (SSDF) and Software Supply Chain Security Guidance. These frameworks help organizations implement robust security practices in software development.
- Federal Trade Commission (FTC). The FTC enforces regulations to protect consumer data and ensure businesses implement adequate security measures. It has the authority to take action against companies that fail to protect consumer data adequately.
- Department of Homeland Security (DHS). The DHS enforces the Protection of Controlled Unclassified Information (CUI), Security Directives for Critical Infrastructure, such as transportation and pipelines, and Cybersecurity Information Sharing between federal agencies and private sector entities.
- North American Electric Reliability Corporation (NERC). NERC develops and enforces reliability standards for the North American bulk power system, including cybersecurity standards to protect critical infrastructure such as Access Control Measures, Incident Reporting and Response, Security Awareness and Training, Monitoring and Logging, Configuration Management, and Periodic Assessments and Audits.
Certifications Imposing Security Requirements
- ISO/IEC 27001. ISO/IEC 27001 is an international information security management systems (ISMS) standard. It provides a framework for managing and protecting sensitive information through a systematic approach to risk management, including people, processes, and IT systems. Pay extra attention to ISO 27001 Annex A 8.26 Application Security Requirements. That is a set of controls that require us to identify, specify and approve information security requirements when we develop or acquire applications. You may hear the term – ‘security by design and default’. ISO 27001 Annex A 8.26 is a preventive control ensuring all information security requirements are identified and addressed when developing or acquiring applications.
- ISO/IEC 27002. ISO/IEC 27002 provides best practice recommendations on information security management used by those responsible for initiating, implementing, or maintaining information security management systems (ISMS).
- ISO/IEC 12207 and ISO/IEC 15288. These standards are crucial for software development and systems engineering, providing guidelines for the lifecycle processes of software and systems, including security considerations.
- ISO 29119. ISO 29119 is a set of standards for software testing that includes guidelines for ensuring software security and quality through systematic testing processes.
- ISO 22301. ISO 22301 is a standard for business continuity management systems (BCMS). It helps organizations prepare for, respond to, and recover from disruptive incidents, ensuring the continuity of critical business functions.
- ISO/IEC 27034 Application Security provides a framework that helps organizations identify and protect specific application’s sensitive information. It proposes components such as Application Security Controls (ASC) and processes to ensure that sensitive applications meet the Targeted Level of Trust (i.e. the required security level). The goal is to ensure that no sensitive information can be accessed, modified or lost by neither any unexpected event nor unauthorized person, internally or externally. Therefore, when ISO/IEC 27034 is well implemented and managed by an organization, it will not only help to provide expected and verifiable evidence to demonstrate that adequate protection of sensitive applications is in place, but it will also help to support the organization’s ISMS and the ICT security.
External security requirements from laws, regulators, and certifications play a crucial role in shaping the security landscape for software development. Organizations must stay informed and compliant with these requirements to protect their data, maintain customer trust, and avoid legal repercussions. This article highlights some of the sources of these external security requirements, providing a foundation for further exploration and implementation.
Interaction of Security Requirements with other Non-Functional Requirements Groups
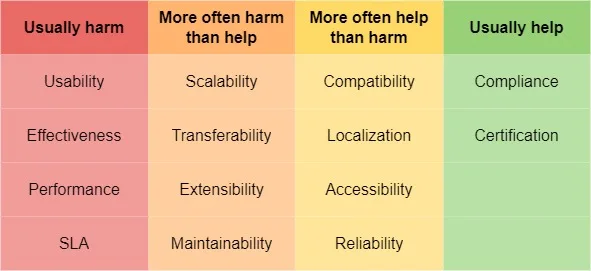
Security requirements can affect other non-functional requirements for the system as well. These inherent conflicts require negotiation. For example, security requirements may require compromises on performance. Usual interactions between Security requirements and other non-functional requirements are:
Requirements that more often help security than harm:
- When compatibility means correct operations, they synergize. However, supporting outdated and not always safe-protocols can greatly hinder security.
- Localisation of storing user data inside his country according to legal requirements is an important security factor. From an organization’s point of view, such data localization may cause additional risks as it complicates the storage of data across multiple countries and data centres interacting with each other. Sometimes, the organization has to store data in places where it has little presence. Such situations may lead to data leakage, industrial espionage and so on.
- Uninterrupted functioning of the means of defence certainly helps security. But to support the continuous operation of functions for users, you may have to sacrifice protection from unauthorised access. Protection from unauthorised access will sometimes interfere with legitimate users.
- Pretty much the same situation.
Requirements that more often harm security than help:
- Portability from one environment to another, extensibility (as the ability to incorporate new functionality), scalability, and maintainability – they share a common problem. The more different configurations a system has, the more environments it can operate in, the more data and operations it can handle – the more difficult it is to address all the security border cases. For systems where serious security is required, the variability of scenarios and circumstances in which the system operates is minimized, otherwise, it becomes too difficult to ensure the system security.
Requirements that tend to get in the way of security. These tend to be the ones with the most problems and need to be paid close attention to:
- Usability usually goes against security. Using passwords, entering one-time codes, and carrying around tokens is inconvenient for the user, but you will have to find a balance.
- Efficiency and productivity often suffer because security measures require computing power and other resources.
- The level of service can easily suffer because necessary checks and security measures will hamper and slow down operations.
To sum up, most non-functional requirements types can conflict with security requirements in one way or another. It should be kept in mind when designing Non-Functional requirements for the system.
In conclusion, the role of a Business Analyst in application and data security is pivotal in ensuring that security requirements are identified and effectively integrated into the overall project framework. By understanding the security nuances, analysts can bridge the gap between technical specifications and business needs. It involves recognizing the potential risks with inadequate security measures and advocating for comprehensive solutions that protect sensitive data and system integrity.